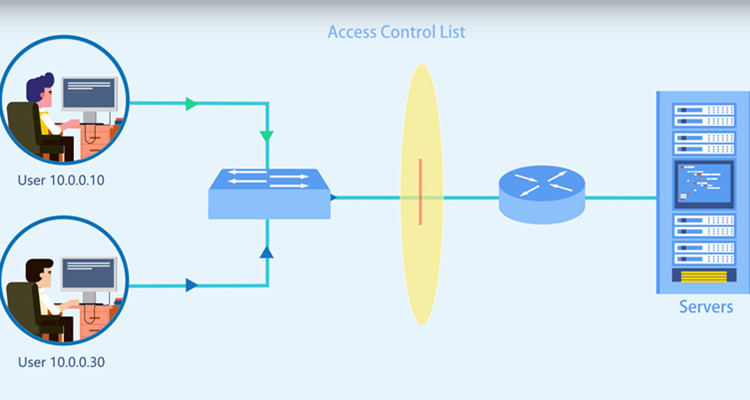
Though the robust network promotes the connectivity among people at every comer of the globe, we may not enjoy its convenience or gain the information we want as easily and casually as it thought to be. Due to the access control list, some paths to a certain server may have been blocked manually. Well, what is access control list? Why does it get in my way to the fantastic world?
What Is ACL (Access Control List)?
ACL stands for Access Control List. It is a list of a series of rules that are specified to permit or deny traffic flow. More precisely, ACL serves to filter data packet based on a given filtering criteria on a router or data switch interface, thereby controlling access to your network or to specific files or folders on your network. How does ACL work? As we all know, when a router receives a packet, it will routinely identify its destination address and find an entry in routing table that can match with it. If succeed, the packet can be forwarded, otherwise, discarded. We can run ACL conditions before or after the router makes forward decision. If deny condition matches, drop the packet immediately, otherwise, move on to the next step as normal.
There are mainly two types of ACL, namely standard ACL and extended ACL. The former one only specifies the source address while the latter can permit or deny traffic based on both the source and destination addresses as well as the ports (for TCP or UDP), or the IPCMP type (for ICMP).
Why Do We Need Access Control List?
First, it works as a security for your network by filtering the unwanted traffic and blocking specific hosts. In the above scenario, if we exclude the ACL, anyone who knows the right destination address can send his packet through the router with no security policy, and damage may ensue. Given this, you can customize ACL conditions to decide who has access to resources in the network.
Besides, ACLs are used for several other purposes such as prioritizing traffic for QoS (Quality of Services), triggering alert, restricting remote access, debugging and so on.
How to Configure Access Control List?
We’ve produced a video for your better understanding of ACL network and ACL configuration. FS S5800/S5850/S8050 series switches are used in this video. Here are the basic access control list commands.
This step helps enter the global configuration mode
In this step, we create an ACL, and its number is “123”. Then we can add rules to the ACL. Please note that ACL number for the standard ACLs has to be between 1—99 and 1300—1999, and extended access list numbers ranges from 100 to 199, and from 2000 to 2699.
Use the host keyword to specify the host you want to permit or deny. This means that deny tcp host 192.168.1.2 access to 192.168.1.1.
The command above permits all message.
Here create a class-map and name it “http”.
Match the access control list of “123”.
Create policy-map “web”.
Associate the class-map “http” with the policy-map.
Enter the eth-0-1 port on FS S5850-32S2Q 10gbe switch.
Invoke the policy table “web” in the inbound direction of the interface.
The series of operations ban successfully the address 192.168.1.1 from entering the switch now.
Conclusion
Having read this article, you may get acquainted with access control list and know how to configure it. The ACL network helps prevent others from entering into your private network space while keeping you out from where others don’t let you in. Everyone can adopt it to manage your own networking condition. In this way, FS provides you with good quality equipment like fiber switch and PoE network switch and best solutions.